Why do Cybersecurity? Can you take a chance on your Info Technology being attacked by nefarious actors?
There are a lot of attackers looking for a way into your computers:
 Including Alias “little Japanese”
Including Alias “little Japanese”
These criminals have honed their skills. “All Your Bases belong to Us” is a video gaming term – where 2 gamers are fighting each other and attempt to take over their opponent’s bases, the term mean that when it was first used but it has morphed as many other things have on the net.
In this case I take it to mean in broken English how Criminals in other countries will take over your computers. They are crafty and have learned their way around computer weaknesses. The hackers are getting better all the time.
So if you decide yes we _will_ improve our security situation … now what?
How much time and resources should be spent on Cybersecurity prevention?
Is it about 10%? For simplicity let’s say 10% is the minimum amount of time and resources that should be spent.
So out of 2000 work hours spent in a year – (i.e. not including all the time sleeping and taking time off) 200 hours per year should be spent on various activities to save your personal and business data from calamity.
Now the big question is what to do with the time and resources to be spent on Cybersecurity? 200 hours is not a lot for the year and it should not be used up all at once as there are other things to do. So if we divide 200 by 12 it equals 16 2/3 hours per month. we can round it to 17 hours per month. it can be about 4 hours per week.
The interesting item as Anthony Christie¹ says: “Our security people spend 60% of their time optimizing documentation and 40% of their time doing the work,” said Anthony Christie, chief marketing officer for Level 3 Communications (a networking company).
So let’s say 2.4 hours on documentation and 1.6 on actual security work.
Documentation is important that is why 60% of time should be spent on it.
This is where Fixvirus.com can help you we are familiar with compliance standards including HIPAA, PCI, NASD, Sarbanes Oxley, GLBA and more.
But what should your IT department actually do? Update your systems – make sure they have the latest patches. Updating your systems is not easy peasy.
Before doing an update one has to test the patch to make sure it will not harm the rest of your software that is run in your standard environment.
PCI Compliance² is important if you take credit card payments.
HIPAA compliance is important if you handle or are near patient data.
Sarbanes Oxley if a public company (Or thinking of becoming one)
Various Financial Regulations require cybersecurity as well for any financial institution.
The consumer rights division is getting more aggressive so needless to say there are many government entities regulating more and more Cyber activities, and _when_ there are more attacks there will be more regulations not less (when have you seen less regulations from the government?). The Federal Trade Commission got a ruling in the Wyndham case³ data security:
“The FTC sued the hospitality company and three subsidiaries, alleging that data security failures led to three data breaches at Wyndham hotels in less than two years. According to the complaint, those failures resulted in millions of dollars of fraudulent charges on consumers’ credit and debit cards – and the transfer of hundreds of thousands of consumers’ account information to a website registered in Russia.”
You can see that as an executive overseeing an IT department one can look at the budget and spend in many directions, including technology.
Remember that technology is just one piece of the puzzle:
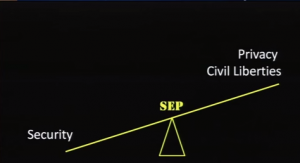
Privacy and civil liberties versus Security needs to be taken into account, your risk assessment must be done by qualified individuals. There is no such thing as 100% security, only “more secure” and “less secure”
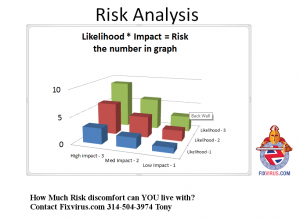
The likelihood of an attack and the impact of the attack (what would happen if criminals are successful) should set your risk and then you can gauge your “Risk appetite” to decide where to spend your budget.
As I have discussed in my blog Website Oversitesentry.com(4)
Here is another way of looking at risk management:
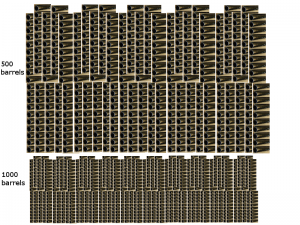
Imagine playing Russian roulette with a 1000 or 500 barrel gun (depends on circumstances)
Every day we are revolving the barrels (1 has a bullet) so we have a 1 in 500 chance(or 1 in a 1000) for something bad to happen. Hopefully the odds are 1 in 500 or 1 in 1000. But imagine the worst possible experience – your customer data is now in the hands of a criminal. Now what?
Whether you know it or not, there are risks just for using your computers and being connected to the Internet. So unless you want to disconnect there will be risks. So what will you do to reduce your risks?
Contact us to discuss