We have to look at patching computers as a defense to potential attacks. To patch computers means to develop a process of updating software that have less security problems. Also while updating it is hopefully still stable(without crashes).
And the reason is many Criminal hacker attacks. Including a Zero-day attack which means an attack on unpatched software. (in the instances where no patch is available) The time it takes you to patch a system and the time a Zero Day attack was released is a dangerous time, since no defense for that software works.
You have to agree that patching your computers is important, and the sooner the better.
Of course the criminal attackers are interested in Zero Day attacks and are buying these attacks in special markets for criminals (like ebay for Zero Day attacks), Darknet has some of these markets
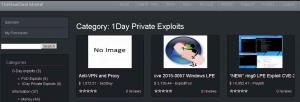
If you notice from above image (from an image at iicybersecurity.wordpress.com) there are 1day exploits as well. which means the fixes have been in the market for a single day already.
When your IT department asks you to install patches and reboot they are asking you to get a fix for a potential attack.
What kind of attack depends on the severity and danger of the software flaw.
There is a system of scoring the severity of attacks called Common Vulnerability Scoring System.
The severity is set from 0 – 10 (Zero through ten). With 10 a severe vulnerability which requires a fix As Soon As Practical.
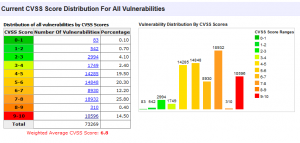
There have been thousands of vulnerabilities in from all software in the last 15 years. The problem that we have is that software is not just the operating system, it is all the applications that run on top of the operating system.
You can see that over the years there have been 73 thousand plus vulnerabilities and most disturbing over ten thousand are in the 9-10 severity range.
This is why many in the Cybersecurity field claim that the offense is winning and the defense is always playing catch up.
As the exploits come out they are called Zero-days, the attackers attack sometimes by buying the exploits from the Darknet. There is a constant fight between the defense which is patching and fixing against potential attacks and the attacker which is always trying to infect your computer with new methods.
This dance between offense and defense will never change (unless we just don’t want to use our computers period). So all we can do is develop risk analysis and put most of our resources into ensuring the most important systems are patched.
Some time ago Microsoft decided to create a single day which would have most of their patches available. This is called Patch Tuesday, and in this Month’s patch Tuesday was December 8th. For December 2015, Adobe and Microsoft plugged over 70 security issues.
Internet Explorer had 30 security flaws
Microsoft Edge had 15 (the new Internet Explorer)
Adobe Flash player had 78 vulnerabilities.
Every month since December 2015 there have been 1000 vulnerabilities per year, so today about 8000 vulnerabilities have been released and patched since then (going well into 9000 of course). It is interesting how things have stayed the same over the years even as software changes and gets updates.
Are you running Windows Server DNS services? there is a patch for that as well which is dangerous, especially since it is on critical servers usually. Although the DNS patch is rated a 2. I am in the belief that the hacker will take any in to your network and then slowly move laterally to other weak systems until getting to the areas which are the true targets.

Your Risk is dependent on impact and likelihood. How important is your server? How important is your database information? What is the impact if you lose the server or software? what is the likelihood of this occurrence?
If you have a severity level 10 vulnerability and its impact is high(if it fails) because of an important software on this machine then decision is easy patch as soon as practical. In fact don’t patch other systems, and you should patch the higher risk machine.
How important is your server?
How important is your database information?
If you have a severity level 10 vulnerability and its impact is high(if your software fails) because of an important software on this machine then decision is easy patch as soon as practical. In fact don’t patch other systems, and you should patch the higher risk machine.
Are we going to run into a resource allocation problem?
Sure the highest impact system will get patched sooner than others. But if there are 70 patches we have to make judgments as to what will be patched first.
The other problem we have is sometimes the patch that is installed has problems so we now have to pick from either of two bad outcomes.
1 is an unpatched system that is susceptible to attacks
2 is a system that is patched but has some kind of bug which means the software will not work as advertised.
We also have a problem when the pace of patching is not fast enough, since tests have to be run before patching (to prevent catastrophic problems).
So the problem is between lack of resources of patching and the attackers finding an attack vector on your machines.
Contact me in the Saint Louis area to help you with risk analysis, systematically patch your computers for compliance and more importantly for a higher level of security.