Here is some basic control theory:
 From book “Modern Control Theory”. (Graduate level course)
From book “Modern Control Theory”. (Graduate level course)
The idea is input R(s) is modified by feedback (the – arrow) thus resulting into E(s) which is simulated as the box and the mathematical formula it represents K/(s-10)(s+20)(s+100)
the end result being C(s)
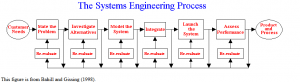
We can imagine the above as the System Engineering process in “the Company System” following:
You can see the control theory in the System engineering process.
The computer can be simulated as well in a system engineering Point of View:
R(s) = human input
E(s) = computer programs
(includes feedback)
C(s) is output that is needed (printout, display, network etc)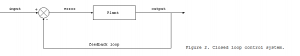 Closed Loop feedback is another method of looking at it.
Closed Loop feedback is another method of looking at it.
The problem that we have is that Hackers are inserting themselves into our processes, whether we like it or not.
Can you truly say with 100% certainty or even 95% certainty that there are no inherent errors in any of your computers, network systems, firewalls (true this is where Risk Assessment comes into play which we can help with).
It is now instructive to note that there are always inherent problems in computers (as mentioned in today’s blog post) http://oversitesentry.com/international-data-privacy-day-is-false-observance/
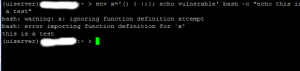 this is the Bash Shellcode command line hack that was found after Bash shellcode was found last summer and culminated in various Common Vulnerability Exposure bulletins (a couple listed in http://shadow-soft.com/bash-shell-code-injection-vulnerability-remediation-rhel-users/)
this is the Bash Shellcode command line hack that was found after Bash shellcode was found last summer and culminated in various Common Vulnerability Exposure bulletins (a couple listed in http://shadow-soft.com/bash-shell-code-injection-vulnerability-remediation-rhel-users/)
what we need is a process which gives the board and the Executive officers a method of testing to prove the effectiveness of the IT department
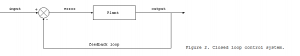 the testing is the feedback the IT department and executives need to run a secure and effective environment
the testing is the feedback the IT department and executives need to run a secure and effective environment
Here is a new blogpost http://oversitesentry.com/?p=1375 explaining why cybersecurity is difficult, as we are trying to check the security of applications and systems in this day and age.
It is important for us to get Security to the next level – with System Engineering.