Don’t waste time worrying – spend time planning for security.
The hackers are challenging themselves to do better – are you?
There must be a will to keep the network defense up and spend the resources for defense. Security cannot be solved but can be mitigated. You can reduce the risk to a manageable level.
The problem is computers are not perfect(configured by people), and we need to use them when we need them… we don’t want to have a problem, we just want to use the computers!
Criminal Hackers are inserting themselves into our processes, whether we like it or not.
Can you truly say with 95% certainty that there are no errors in any of your computers, network systems, firewalls or WiFi access points? (A Risk Assessment may be needed which we can complete).
Instead of looking at Cybersecurity as an expense or act like it is in the way, it has to be looked as a must do. (You do not want to be Hacked and then it is too late like I discuss in my book “Too Late You’re Hacked” )
Here is another attempt at trying to explain the Psychology of Security: Part2 Let’s Try this Again
The issue is our psyche is predisposed to take more risks when it costs us something to try to lessen a possible higher risk. I.e. if it costs $500 to try and not losing $1000 we try to not spend the money/time cost.
The interesting thing in our age of email spam and ransomware the chances of getting hit with ransomware are much higher than you think. And the possible failure of defense (meaning ransomware attack can close your business if a backup is not tested). Testing a backup may cost money and time, but it is worth it. because if it does not work you have lost the data (that you thought was backed up).
here is the infographic created:
This is a complex topic and we can help you
With the right circumstances there could be a failure in your security and thus a loss in that you may not be able to fathom right now. It takes months to find a break-in and by then the damage has been done. Check if your email has been compromised at Have I been Pwned?
Last year’s blogposts on my blogsite(Oversitesentry) on the SolarWinds debacle: https://oversitesentry.com/what-happened-to-solarwinds-hack-effects/
If you are interested in how hackers make money as Ransomware infestations around the world show this. Check one of our blogposts at Oversitesentry .
One of the latest blogposts(3/24/22) discusses Vulnerability management at oversitesentry :
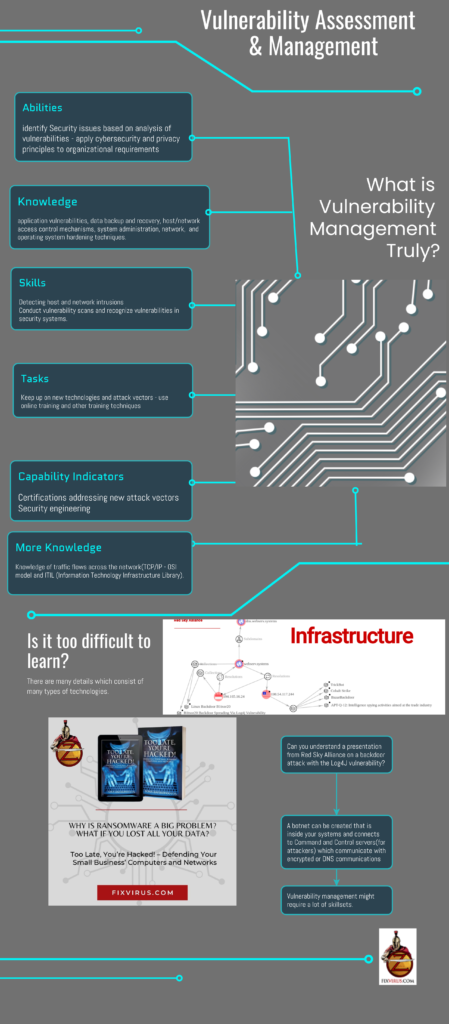
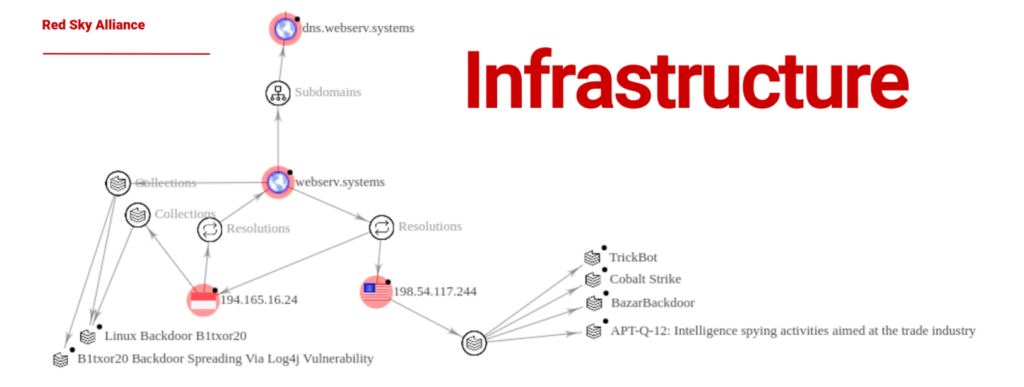
Can you defend your environment against this botnet and Command and control server?
Contact Us to discuss improving your security auditing your critical computer resources.
Certified Information Systems Auditor
Page updated 03/24/22

Pingback: Wifi Attacks Succeed Against WEP/WPA | Oversite Sentry
Pingback: Wifi Attacks Succeed Against All:WEP/WPA | Oversite Sentry