Every environment is different. You need to decide very carefully on how to set up this log analysis method, as every action can be used against you. And don’t forget that not every attack is a dangerous cyber attack.
There should be automated methods of log identification and filters set up to find malware.
The key is to be prepared for an attack and set up the proper resources for what is needed at every step.
First Emphasize that Log Analysis purpose is to find attacks from criminals outside and from inside the network.
Collect data and send to a log server.
- Set up a secured device inside the network with limited access (at most 3 people in org) to store logs.
- Set up Filtering scripts to sift through the logs and find server or application access
- Set up Firewall Rules using firewall vendor that claim they are attacks
- Set up a weekly event analysis meeting – to review alerts that are flagged by the current system and scripts.
- Improve alerts using the alert review – to reduce noise and improve actual attack notification. Improve the scripts to reduce noise
- Repeat steps 4 and 5.
- Set up a yearly review of the whole system to see if any major changes should be done.
Obviously this is not a small project – and there are ways to connect to Splunk or vendors that perform log analysis. Even though every environment and situation is different the general idea is to have a system of:
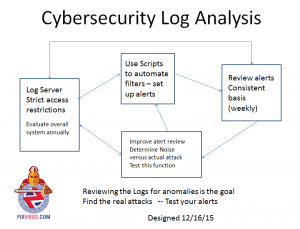
- Set up an automated method with scripting or other method
- review the alerts on a weekly basis
- Improve alert review to reduce the noise and find the real attacks.
repeat steps 1-3 logging and alerting automation and review by testing.
If attack found start incident process (if no incident process set one up now).
Remember that even with Compliance it does not mean one is secure. And don’t forget to test the best alerting you have and when you think you can find anything … Hire somebody who will prove you wrong.
The Attack characteristics are similar to other malware like cryptowall.
The Initial attack vectors need to be reviewed to check our logs for IOC’s
- remote access scenarios
- Internet facing systems with weak authentication
- Botnet infection
- exfiltration occurs via ports/services commonly associated with data transfers.
- ICMP — TLS/HTTPS — NetBIOS — SSH — FTP/SFTP
We have to create a baseline and then do checks on the traffic.
The verbal discussion centered around a specific point of traffic from inside to out that needs to be alerted:
Outgoing FTP (File Transfer Protocol) traffic. It seems that malware authors prefer simple methods. And they no longer upload during 3am time slots. so time-dependent alerts may have less meaning.
So you have to ask yourself – how often does the company as a whole upload ftp traffic? Even if you want to allow it in general – create an alert and review it every week. It is worth it.
Contact Me Tony Zafiropoulos 314-504-3974 for an initial discussion.