This page has technical background information on the hacker attack cycle – click here to go back to home page:
The criminal hacker is ultimately trying to access and then control your computers, this process has been catalogued in many different ways, but the end result is the same – the criminal wants your resources.
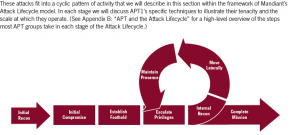
The above diagram is from Mandiant’s thorough report Mandiant APT1 Report on how Chinese hackers stole data from US companies.
We translate this diagram into easier to understand English as it is important to know what the attackers will be doing in our networks.
SVAPE & C
Scan first (check what ports are open – tcp/udp 1-65536 – there are 65536 ports on the IPv4 standard as 2 bytes create the number 2^16=65536) doing an initial scan allows the hacker to plan the next moves/
Vulnerability Analysis Analyse the port and review how it behaves, assess the potential attack angles)
Penetrate (use the Vulnerability analysis to find an attack that wil succeed)
Exploit (attack and get on the system)
& Control (keep accessing the hacked computers)
The criminal hacker has a goal and the goal is to attack and control the computer. In the future the criminal hacker can then sell this control, either to attack other computers or to sell the rights to it.
There have been instances in the past where a piece of malware did not do much right away. Only after some time the criminal software downloads more software for cryptolocker for example. Now your system has Cryptolocker because it was sold from one criminal hacker to another (in the Darkweb)
And as you may know once your system has Cryptolocker (ransomware) your world changes as all your files become encrypted and thus unusable without a decryption code which has to be bought from the criminal. Paying the ransom does not guarantee decryption.
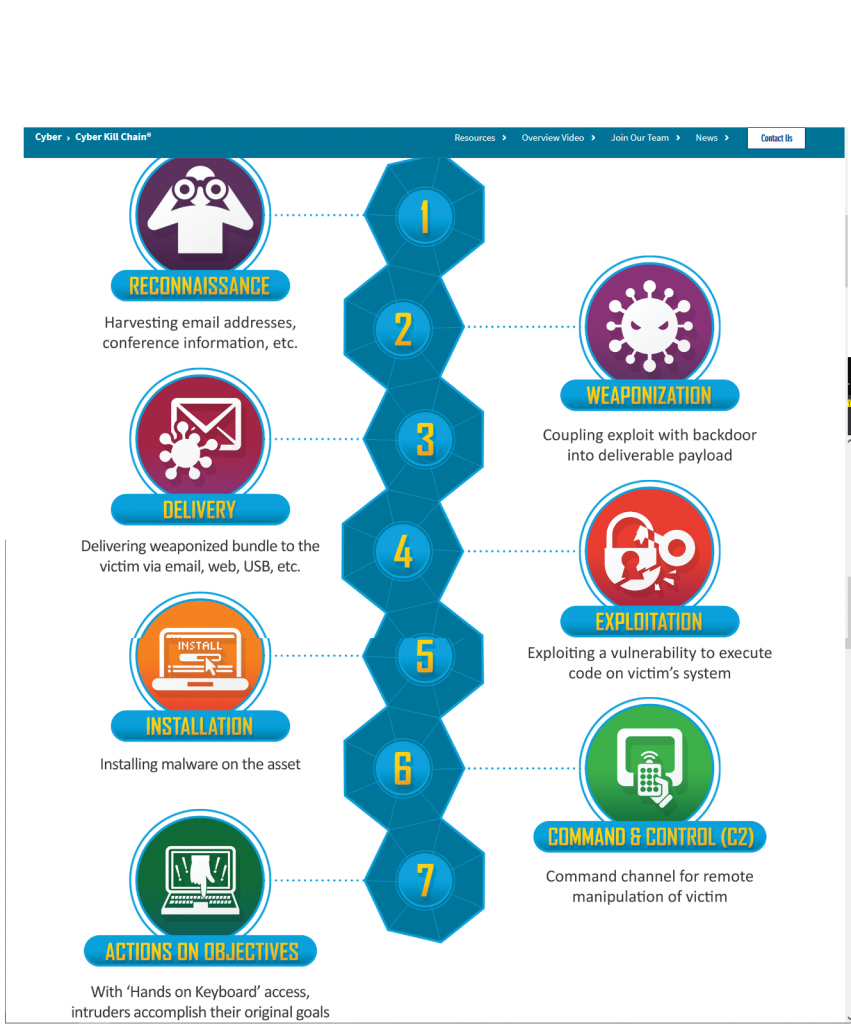
There are other companies that have made a pictorial representation of this attack cycle:
Lockheed Martin has copyrighted the “Cyber Kill Chain” I have added the image from their website below. Notice the similarity of many of these systems… (another one comes to mind from https://attack.mitre.org/ Which goes into more detail)
they are all the same – look first (recon or scan), then review for attack (vulnerabilities), then attack, then penetrate and stay in the network.
DarkWeb discussion on our Blog post from May 27, 2015: http://oversitesentry.com/darknet-know-it-learn-it/
Newest Blogpost on SVAPE&C
How Can You Tell If Hackers Are Hacking You?
Last updated 11/11/2024

Pingback: Linux Servers Can Get Malware Too | Oversite Sentry
Pingback: BBQSQL – for Delicious SQL Injection Testing | Oversite Sentry
Pingback: How-Why Hackers Do What They Do? | Oversite Sentry
Pingback: Can you be 100% sure that your network and systems are not vulnerable?
Pingback: Criminal Hackers Have 1000% ROI on Ransomware & Exploits | Oversite Sentry
Pingback: We Depend On IT Competence & Reliability | Oversite Sentry
Pingback: BlackHat Presentation: WMI Architecture Used to Attack | Oversite Sentry
Pingback: Adding Pages Redesigning This Site – Fixvirus.com
Pingback: How Do Hackers Do What They Do? – Oversite Sentry
Pingback: Diamond Model Intrusion Analysis | Oversite Sentry
Pingback: Are You Safe From Hackers? | Oversite Sentry
Pingback: Worried About 0Day Attacks? Take Care of 30day first! | Oversite Sentry