What Do I mean when I say “Start With Some Cybersecurity”?
At Fixvirus.com we will help you design your own Cybersecurity department, or help you with just enough Cybersecurity.
What do i mean ‘with just enough Cybersecurity’?
I think it is safe to say that most of us do not think about the security of our phones, computers and tablets. As a whole people want their electronic devices to work.
Is this indicative of what we want in our companies? Do we expect the IT department to keep us safe and secure? We don’t want to think about this we just want it to happen.
So what to do? Why does the IT department need oversight? Because testing their abilities in a nice way tells them they are doing a good job and tells you the IT job is being done well.
You can still get hacked, but at least the i’s were dotted and T’s crossed.
The key in our environments anyway is what happens after the hacker is in. You don’t want them to steal anything and get away with it. You have to set up methods to track down when a hacker is doing their work and shut down the exfiltration (or stealing of data to an external machine).
So to start we have to audit the environment and count all the computers before doing the next steps.
- audit environment – count the computers, find out what is running on the computers. (count computers = find them all and review what is running on them)
- Audit the software since just knowing what hardware or in virtual machines, the instances of servers is not enough. We must know the type and version of software running, since a vulnerability alert can cause PCI compliance to be in jeopardy. The criminal hacker is looking for your software, so you should know what is in your environment as well.
- Doing vulnerability assessments means trying to uncover unpatched software in your environment. ( just like the criminal hacker would do and like you are supposed to do for PCI compliance – HIPAA compliance and all other governance) as it only makes sense.
- What about the Zero-day attacks? the attacks that cannot be patched? Since the hackers found a problem that can be exploited. Well for these situation we have to have a detect and monitor program. Check the logs, check the network traffic (which means a SIEM – Security Information Event Manager) and IPS (Intrusion Prevention System).
- Although the SIEM-IPS systems will not prevent all attacks, they will prevent a lot and with vigilance we can keep up with attacks on our environment with enough resources.
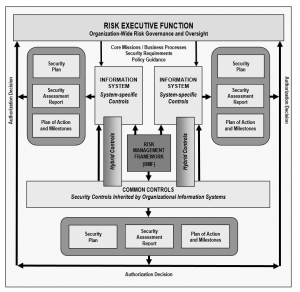
[Image from NIST(National Institute of Standards and Technology) 800-37 documents¹]
If risk management is to work properly in an entity it must be assessed given enough time to review all your data and usage of computers.
So yes the first thing one must do is to find out what and how your Info tech is being used. so don’t just learn what is running on each computer, but rate each item to its risk factor:
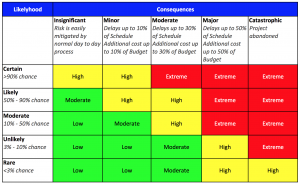
You must classify data from High importance, to Low importance.
High Importance data can then be properly classified in Cyber Risk categories.
We will review each step of the path to better Cybersecurity again and again as that is what we are all about.
Contact us to discuss Contact me Tony Zafiropoulos 314-504-3974
Our hashtag #testYourSecurity should be everyone’s hashtag that wants more Cybersecurity.