What does it mean to be PCI compliant? Are You Secure if you passed compliance standards?
If you update your software as you are supposed to be PCI compliant what happens if the update breaks your environment or is actually not secure?
Do you need an example? How about from our blogpost¹:
In our blogpost we mention a plugin that was hijacked by a criminal then he installed his own malicious code in the plugin.
Now he said “Upgrade your plugin” to WordPress which caused WordPress program organization through it’s upgrade mechanism tells all the users of the plugin to upgrade.
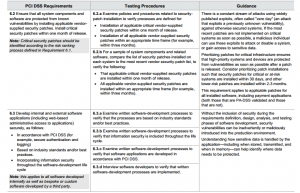
If the unsuspecting users upgrade then they are automatically hacked – Upgrading is normally good, but there has to be a reason for an upgrade and it has to be tested. But for “PCI compliance” you have to upgrade and keep your systems patched for example requirement 6.2 in the latest v3.2 PCI standard²:
Requirement 6.2 Ensure that all system components and software are protected from known vulnerabilities by installing applicable vendor supplied security patches. Install critical security patches within one month of release.
So the Requirement has no mention of fake upgrades only to upgrade your software that is necessary for the systems that need it.
This is why one has to test the upgrade first, make sure it is what it claims to be before placing it in production.
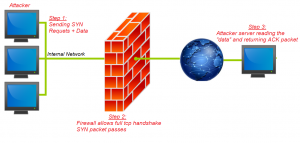
Another problem can be if you are compliant for all “Known” vulnerabilities that means unknown vulnerabilities can hack you even if you are compliant³.
As in the post from Dec 10, 2015 new exploits are found which cause you to get hacked and then you still lose a lot of money even though you have the latest patches. Even in the latest firewalls (like in the post mentioned) certain NGFW Next Generation FireWalls can get hacked with a specific method.
So to answer the question above (are you secure if PCI compliant) not necessarily. In the end PCI compliance is a specific standard for the credit card numbers. You can be compliant for the credit card numbers or Primary Account Numbers(PAN). And still fail to provide security on other systems. Or you can claim to pass the PCI compliance online while not actually performing all the functions.
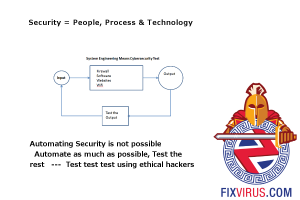
Testing your network for security vulnerabilities should be done by a separate pair of eyes.
- http://oversitesentry.com/new-pci-compliance-v3-2-now-published/
- https://www.pcisecuritystandards.org/documents/PCI_DSS_v3-2.pdf
- http://oversitesentry.com/nextgen-firewall-flaw-uncovered/
Contact me at 314-504-3974 Tony Zafiropoulos to discuss