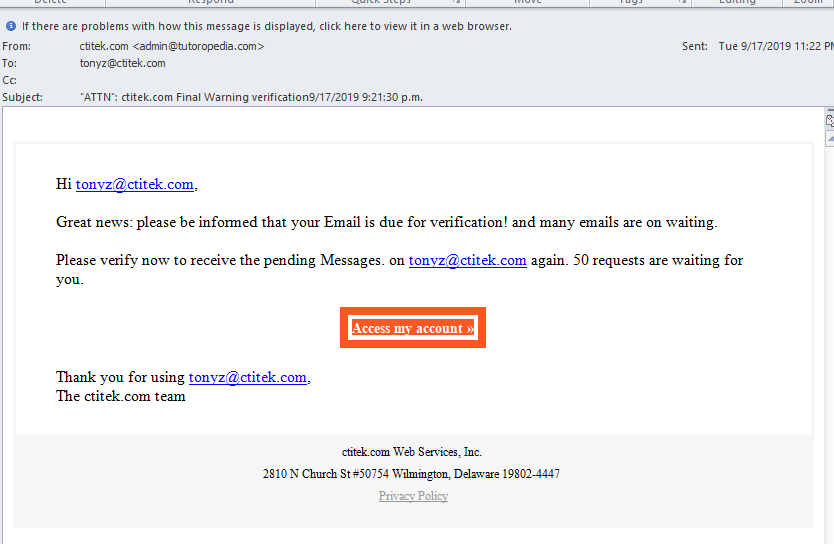
What if you could see some examples of real life attacks? What about a phishing email attack? Do you know the parts of an email that can be changed and can look like anything a creative mind creates?
For example: your email is name@company.com the creative attacker can “spoof” or fake the email coming to you and it can say bigcheese@fakecompany.com
A Guide to my book “Too Late You’re Hacked!” is now available as it has been finally printed.
Go here to order your copy: Guidebook Link to Publisher
Examples such as this one are broken down to review why it is a phishing scam email. Not a real email.