It is May 6th, 2025 and the annual DBIR (Data Breach Investigations Report) is out by Verizon!!
Every year Verizon catalogs the number of breaches that occurred with the clients and otherwise information that is available(although the data was reduced this year fro some reason). And it never fails it is always worse this year than last. And even if the numbers do not actually state it is worse, the overall report makes it seem that way. This phenomenon is typical and unfortunate. What should we really look for in these yearly reports? New trends and old trends, i.e. what do we need to focus on with our defense?
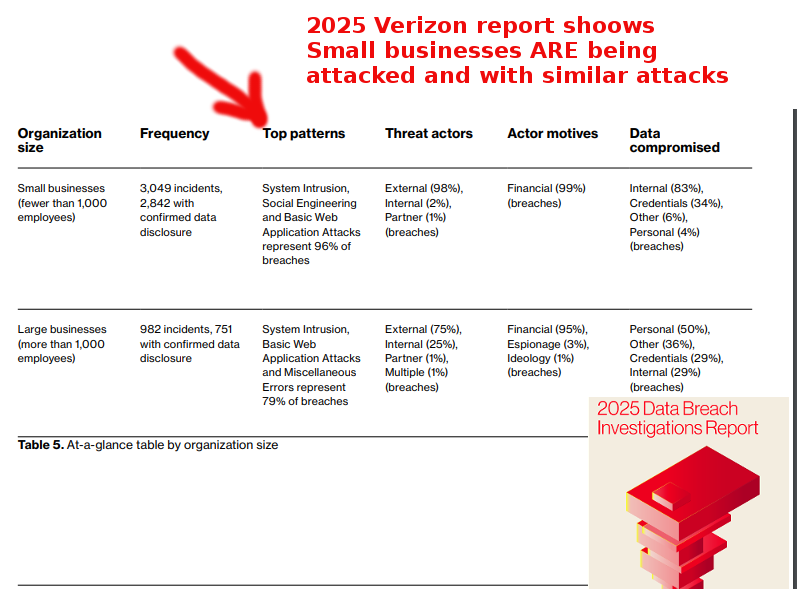
Here is the main point on page 85 in the table: System Intrusion, Social Engineering, and Basic Web Application Attacks represent 96% of breaches
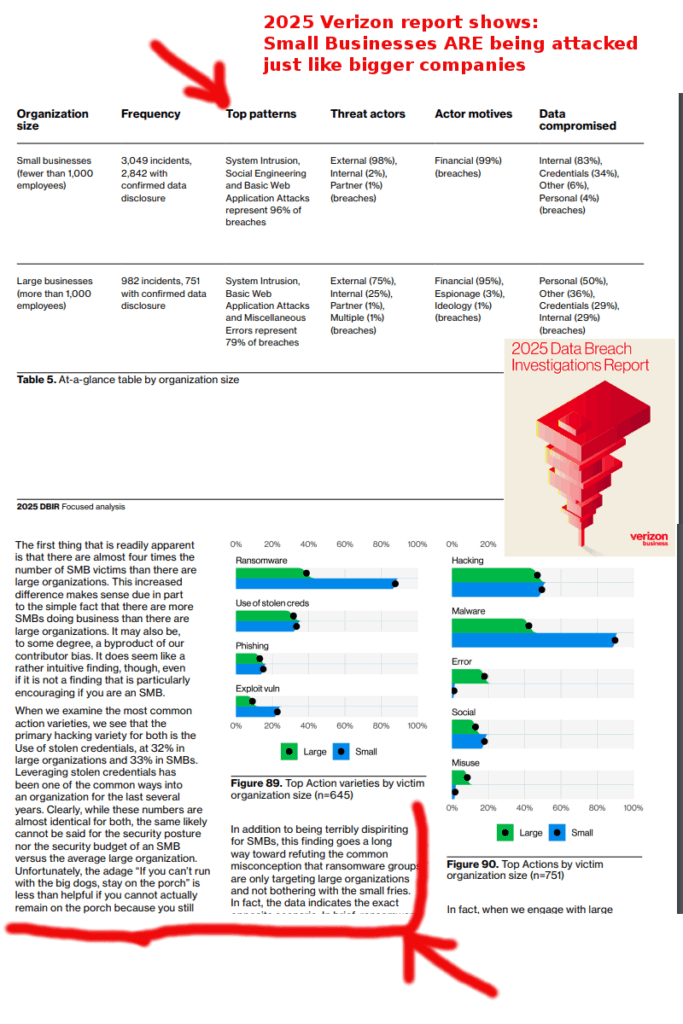
“The first thing that is readily apparent is that there are almost four times the number of SMB victims than there are large organizations. This increased difference makes sense due in part to the simple fact that there are more SMBs doing business than there are large organizations. It may also be, to some degree, a byproduct of our contributor bias. It does seem like a rather intuitive finding, though, even if it is not a finding that is particularly encouraging if you are an SMB.”
ON Page 86: “Whereas large orgs see Ransomware only comprising 39% of the breaches, SMBs are experiencing Ransomware-related breaches to the tune of 88% overall. Speaking of adages, “When it rains, it pours” comes immediately to mind. In addition to being terribly dispiriting for SMBs, this finding goes a long
way toward refuting the common misconception that ransomware groups are only targeting large organizations and not bothering with the small fries.
In fact, the data indicates the exact opposite scenario. In brief, ransomware groups don’t seem to care what size an organization is; they are quite happy to
breach smaller organizations and adjust their ransom demands accordingly.
At Fixvirus we always preach good security practices as even a small environment will get hacked since the attackers (criminal hackers) are paid to hack and take advantage of mistakes and possible problems including social engineering and system intrusion attacks. Here at fixvirus we do not focus so much on the negative.. we like to focus on what you can do to prevent attacks.
Basically the 3 essentials: Update, scan for vulnerabilities, train employees social engineering and security policies for the employees.
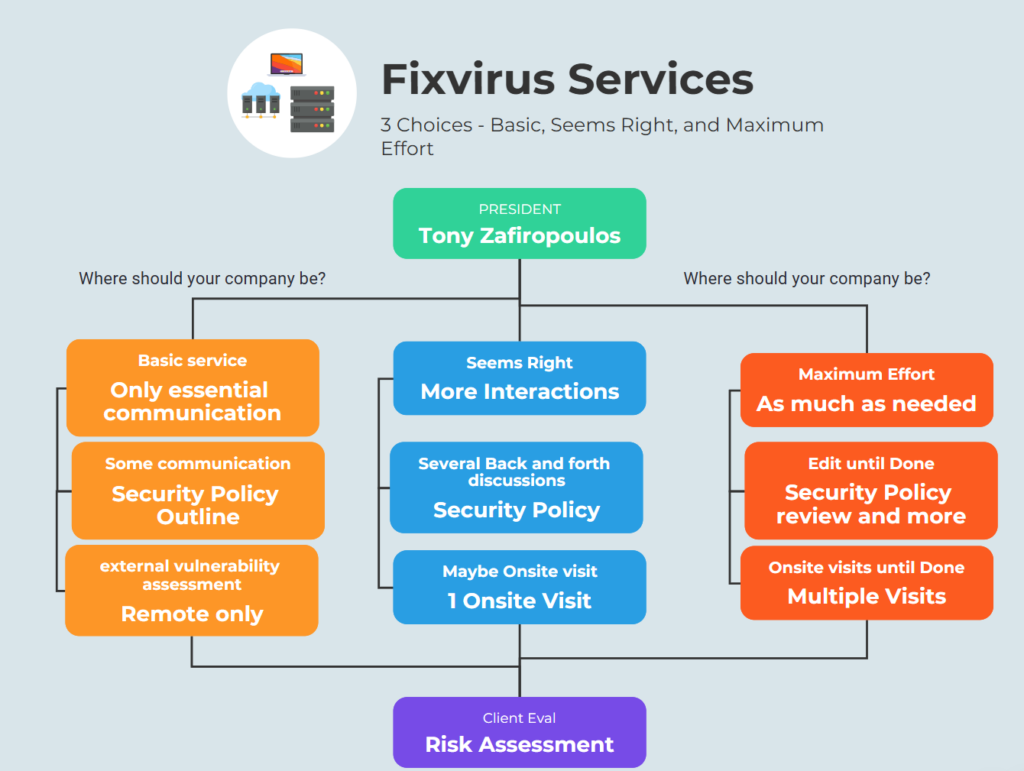
We spend time and resources only when necessary – within an ethical manner. Ethics in cybersecurity and IT is ultra important, as it drives trust and is needed for some difficult choices at times. Contact Tony Zafiropoulos to discuss how we can help you.
Choose between basic , seems right , and max effort:
Basic – Security Policy outline – 1 external vulnerability assessment
Seems Right – Security Policy Outline and 2 passes (back and forth with client to improve Sec Policy) external vulnerability assessment depends on setup may need onsite visit(at least 1 hour onsite visit) and write 1 report.
Max effort – Security Policy Outline plus 10 passes (or as many as required – discussions and Q&A), as many onsite visits as necessary to fully evaluate and write reports as needed.
It will not take long to make a difference – and now you can spend time on on other matters – to grow business or otherwise.
Your Business. Your Customers. Keep Them Safe Online.