Origins of Government Fraud
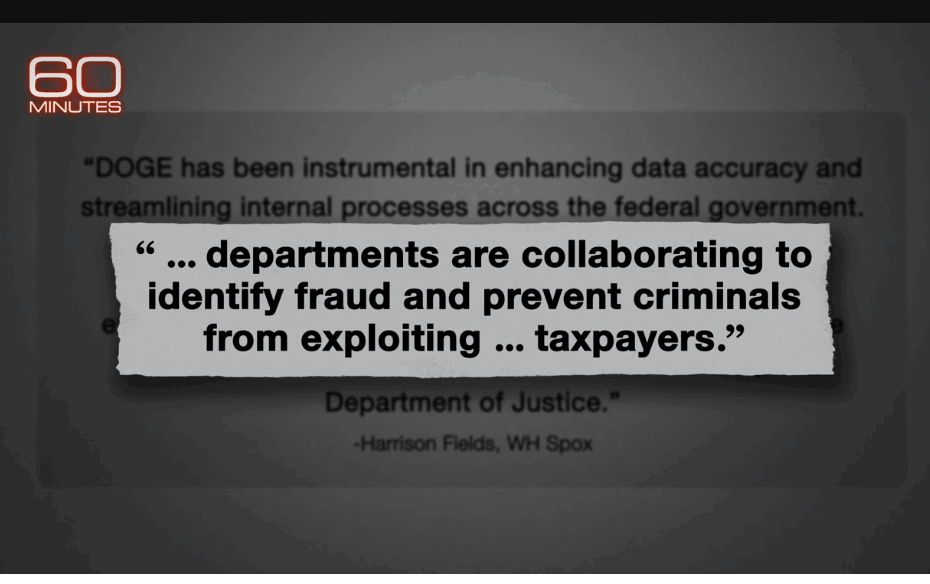
What do you think the original problem of Government fraud would be? Is it government incompetence? Willful corruption? How about the simplest answer(in my mind) … according to CBSNews 60 minutes video and article. “The… Origins of Government Fraud