How I help my customers use consistent methods to stay out of the news (i.e. reduce risks and not get hacked).
We use TTP or Tactics, Techniques, and Procedures to help companies stay safe in the complex world of cybersecurity today.
Use Tactics to help prevent cybersecurity vulnerabilities from invading your machines. (scan all systems and check for vulnerabilities). It depends on your environment and the amount of changes you do on how often it should be done. For some smaller clients we do scans on a yearly or quarterly basis. For larger and more dynamic clients set up an onsite system with automated scans and can run them as much as one wants (at minimum weekly). Some devices can be scanned daily.
Techniques: what software do you scan the systems and when a vulnerability is found what should be done? If a high vulnerability resolve as quick as one can within reason. It all depends on the system.
Procedures: are what you do day after day, which leads to weeks and months. What do I mean? If you have Microsoft software which is likely, then you are beholden to the Patch Tuesday update cycle(every 2nd Tuesday in the month has new Microsoft patches out) which will cause you to test (hopefully) to make sure the patches work in your environment. that means that the earliest you are patching is Wednesday or Thursday. Are you going to let the IT staff reboot right away or on the first or second weekend after they tested? So now the environment is weaker due to your procedures. Should we just install patches as they come out, well that is also unstable. So there has to be a middleground or a “It depends” procedure on the software that needs to be patched or upgraded.
Of course the defense (or blue team) has to contend with the red team or attacker TTP as well:
From infoblox website blog.
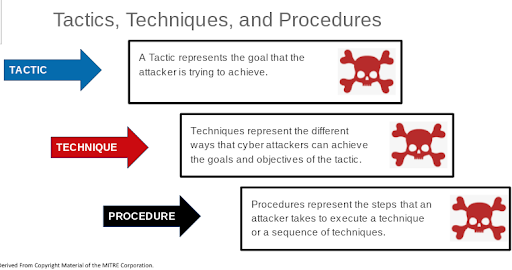
In the tug-of-war between Attacker versus Defender who will have the upper hand?As Defenders we have to be aware of several attack possibilities: Phishing Attacks (which can start all of these attacks), Ransomware deployment(can be alleviated by patching and more), Network Intrusions require vigilance and correct configurations, and Data exfiltration. One needs to monitor the firewalls for unusual traffic.
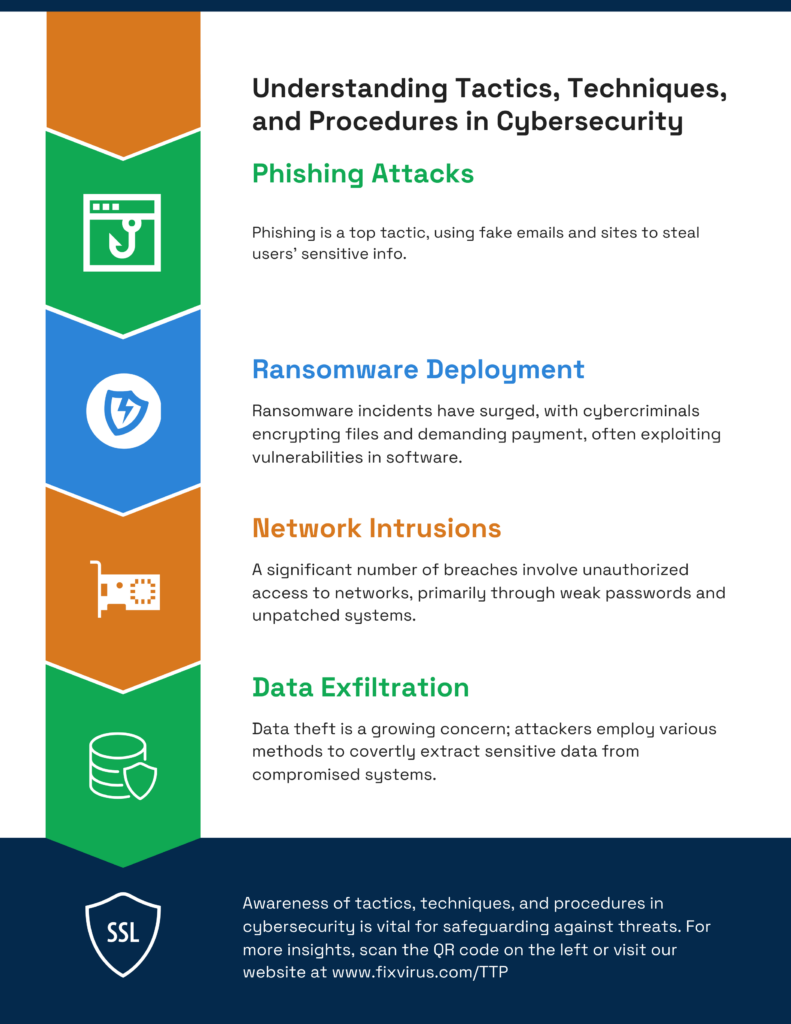
It is imperative to develop TTP’s with up-to-date technology and processes testing the company capability of the basics. The key is to test systems for vulnerabilities and configuration errors on a consistent basis.
Contact to discuss.
