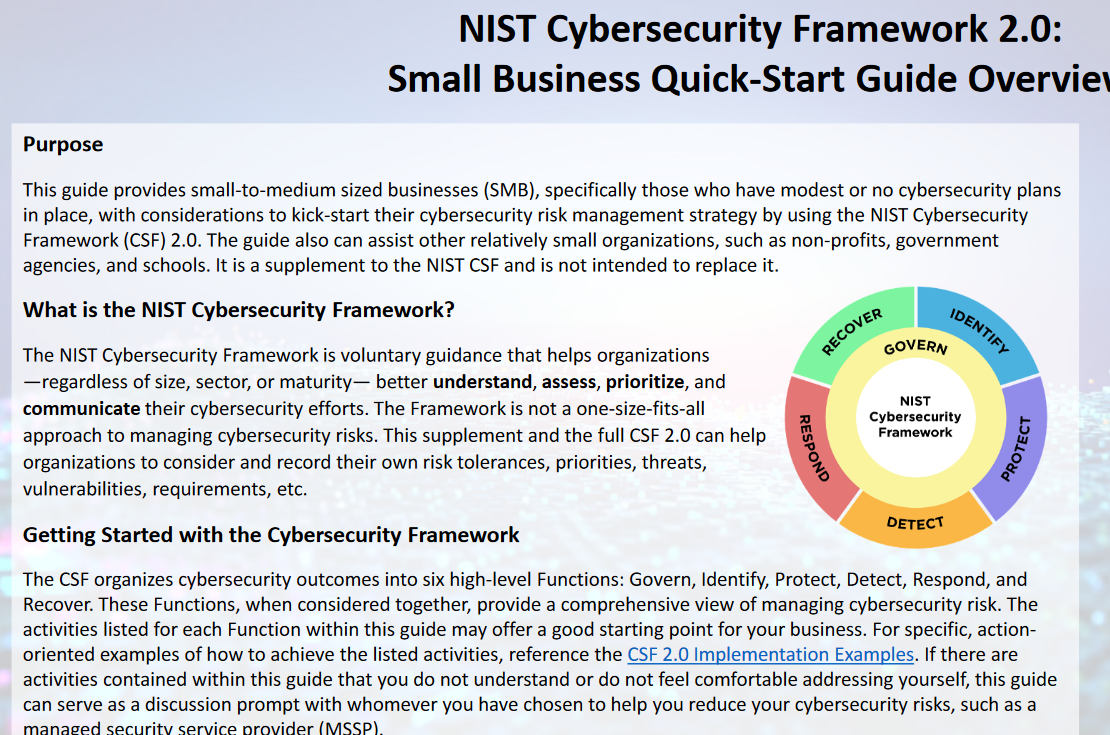
Create a Security Policy using NIST framework
NIST Framework is a good base to create a security policy. I have discussed NIST Framework at my blogsite (oversitesentry.com) and there are 6 pieces to the framework: I have also discuss NIST framework on… Create a Security Policy using NIST framework