What has to happen to have a successful cybersecurity program? It does not have to cost a lot…
- Stay out of news and do not fall for phishing and other scams. set a security culture (as minimal as you want – or as much as), create a security policy, set up training and more.
- Of course have anti-virus or Endpoint Detection & Response (EDR) software as it is termed now.
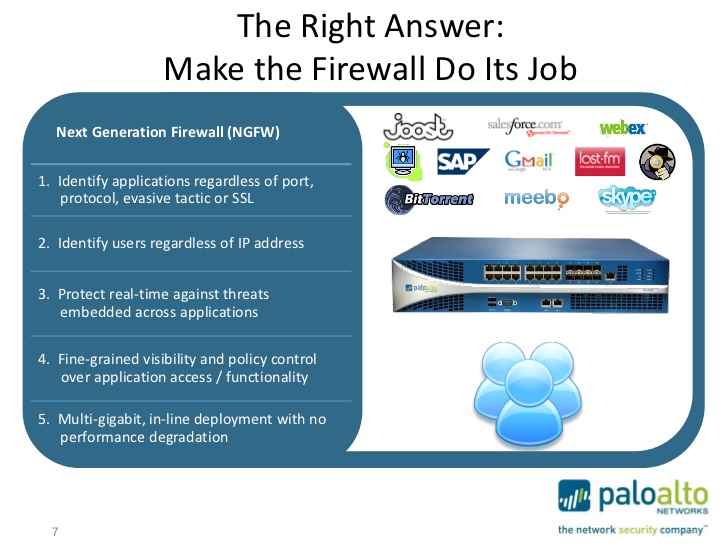
- Firewall or preferably an IDS (Intrusion Detection System) what just recently was called a next gen firewall.
- Vulnerability Management as well
Lets set this with numbers 1-4 EDR, Firewall, Security policy-training, update systems.
1. Protect Your Devices: Antivirus & EDR
- Install reputable antivirus software on all computers and devices. This helps detect and block malware and viruses. Some like malwarebytes.com
- For enhanced protection, consider Endpoint Detection and Response (EDR) solutions, which provide more advanced threat detection and response capabilities than traditional antivirus .
- Keep all security software updated to ensure you’re protected against the latest threats .
2. Secure Your Network: Firewall & IDS
- Use a firewall to block unauthorized access to your network. This acts as a barrier between your business and the internet . (or you can just use the firewall
- For added security, deploy Intrusion Detection Systems (IDS) or Intrusion Prevention Systems (IPS) to monitor network traffic for suspicious activity . Preferably get a firewall with both functions (Palo Alto does this for example)
- Secure your Wi-Fi by using strong encryption (like WPA3), changing default passwords, and hiding your network’s SSID .
3. Establish Security Policies & Train Employees
- Create a simple security policy that outlines acceptable use of company devices, password requirements, and procedures for reporting suspicious activity .
- Train your employees regularly on cybersecurity best practices, including how to spot phishing emails and avoid social engineering attacks .
- Make sure everyone knows not to click on suspicious links or share sensitive information with unknown contacts .
What is your security culture?

4. Patch and Update Systems Regularly
- Enable automatic updates for operating systems, applications, and security software to patch vulnerabilities as soon as fixes are released .
- Regularly review and apply patches to all devices and software, prioritizing critical vulnerabilities .
- Part of review means use tools to test your systems for vulnerabilities – like the free version of Greenbone Vulnerability Management software on Kali Linux.
- Don’t forget about less obvious devices, like wifi, printers and network equipment, which also need updates . And of course the other IoT devices – like TVs, and other UPS(Power supplies) systems. Any system that is on the network is a possible weakness – like a few years ago when a water sensor that checked the heat of a water tank with fish in Las Vegas caused a hacking situation because of it’s vulnerability.

The good thing is that Kali Linux and Greenbone vulnerability management is cheap ($0). Obviously one has to download, install and learn the software, but how hard can that be?
If you are at all wondering how your systems look you should test the systems by running vulnerability management software. Create a security policy and train your employees!!
