Asking Grok :”How much Cybersecurity effort and what is highest risk for a small business?” (next is the answer with a slight distillation – as LLM AI tends to be wordy):
Here is the specific question(higher specificity for LLM AI the more it will reduce hallucinations) “What is the highest risk to a typical company in cybersecurity aspects for the company. I.e. what should be spent time on and how much time. Or just spend time in sales, ops and other parts of growth?”
Using AI in this fashion requires only a little rework – as I do know the answer, but it is good to see the research and links with less effort on my part.
For a typical company—say, a mid-sized business in non-regulated sectors like retail, tech, or services—the highest cybersecurity risks in 2025 revolve around a few persistent and evolving threats that can lead to data breaches, financial loss, operational downtime, or reputational damage. Based on recent analyses, the top risks include:
- Ransomware attacks: These remain the most prevalent and damaging threat, often encrypting data and demanding payment, with a surge in sophisticated operations targeting critical infrastructure and businesses of all sizes. (from vikingcloud.com – cloudsecurityalliance.org, and checkpoint.com)
- Attackers increasingly use AI to automate and personalize these campaigns, and recovery costs can average millions.Phishing and social engineering: Human error is exploited through deceptive emails, texts, or calls, leading to credential theft or malware installation. This is exacerbated by AI-generated deepfakes and convincing scams, with cyber-enabled fraud on the rise. (from above links plus reports.weforum.org , and connectwise.com)
- AI and shadow AI vulnerabilities: Unsanctioned use of AI tools by employees can introduce risks like data leaks or biased outputs, while attackers leverage AI for more effective breaches. (kpmg.com, jpmorganchase.com, and ibm.com)
- Supply chain and third-party risks: Compromises in vendors or software dependencies can cascade to your operations, as seen in high-profile incidents.
- Cloud misconfiguration issues: As more data moves to the cloud, improper setups lead to exposures, alongside DDoS attacks that overwhelm systems. (previous links and forbes.com)
Thus the attack risks are Ransomware attacks, Phishing, Misused tools (AI), 3rd party or supply chain risks, and basic cloud misconfiguration. Makes sense that ransomware are the worst risk
Remember “The Cloud” is just a computer run by another entity – there is no guarantee of perfect defense by the cloud. Here is an example: https://www.wired.com/story/a-dhs-data-hub-exposed-sensitive-intel-to-thousands-of-unauthorized-users/ This story outlines DHS equipment misconfigured to allow private information not to be secure as it should be.
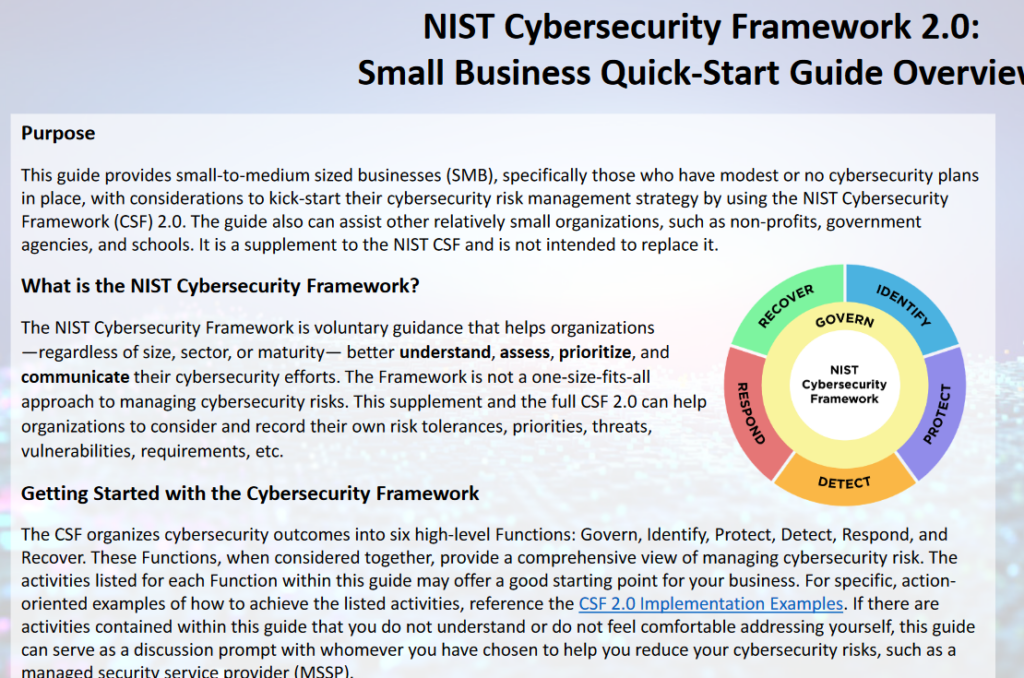
We see the challenges (more ransomware – phishing attacks), and these attacks are becoming more sophisticated. Every year it is becoming harder not easier.
Besides how much money, also where to spend the resources is important. If you look carefully at the Cybersecurity Framework by NIST (above image) the sections divide into Govern, Identify, Protect, Detect, Respond, Recover.
Most entities spend time and money on Protect, Identify and Detect. respond and recover will hopefully never be used right? Or we will just figure it out when it happens.
Sure Govern and Identify kind of goes together (have to know what you have to govern it). And Detect and Protect could be considered similar too.
If one goes into some detail the firewall becomes a must, and some tools to manage devices which can straddle several sections.
Where does phishing attacks get placed? We may misunderstand Governance or at least not pay a good amount of attention to it.
The CEO or CFO who is primarily driving the Information Technology Security direction is at a fork in the road who has to trust someone (the CIO or CISO?).
NIST has compiled all of the sections that need to be done – So someone(whoever that is) has to make the decision to create the direction and resource outlay for cybersecurity. Because if you do not have a comprehensive strategy the result can be as this company unfortunately got hacked due to weak passwords:
You should spend time and effort to create a proper program that covers all risks so that you stay out of the news.
I know currently AI or Artificial Intelligence is getting plenty of hype even though it is a large marketing term that encompasses many AI software systems not just the one that everyone is familiar with. I use Agentic or LLM AI in many ways to help clients… There are always distractions… But we have to spend time and effort on Cybersecurity or the adversary has a say in your operations anyway!
Also use my Top30Security News Analyzed page(at oversitesentry.com) to keep up on cybersecurity news.
Here is the link to the Fixvirus.com security show (video)
Contact me to discuss your cybersecurity direction and plans for the present and future.
